call us at: (248)602-2682 OR Schedule a time to meet with an advisor: Sonareon Schedule
Attend our upcoming Workshop March 26 either at 10AM or 1PM. Register today - $99. Get free AI Assessment.
The Unseen Spill: 7 simple ways data is left exposed in Financial Institutions
7 application capabilities that secretly endanger data privacy and compliance
Peter Serzo
11/9/20252 min read
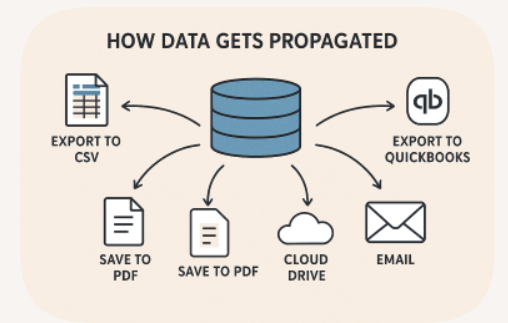
Clients do work with you because you have built trust with them. In a world where parents typically don't share their finances with their children, it is taboo to share what you make with your coworkers, you know it all. You may be a tax preparer, mortgage lender, bank, or a investment company. This post is to make you aware of the 7 simplest ways that everyday applications expose data.
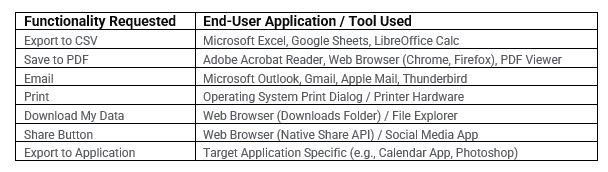
Export to CSV: This has existed for decades in excel and other application. Your folks use it today. However, it created uncontrolled, copyable files (data sprawl) that lead audit trains and access controls behind. Often these contain sensitive data containing Personal Identifying Information (PII). These files can leave a company via email, cloud drives, USB, or into other vendor packages.
Share Button: This seemingly harmless button is found in several applications like Microsoft. This instantly bypasses access controls by creating links and providing permissions that extend beyond the intended users. The ease of distribution makes accidental exposure to third parties likely and undermines core data principals such as least privilege.
Save to PDF: This is a snapshot of sensitive data which is now portable and copyable. Hidden data is often retained in the metadata that can reveal more that the visible content.
Export to <<Application Name>>: Exporting data into an application is a transfer of potentially sensitive financial and customer records. If not done correctly one could have mismatched mappings or ports can expose extra fields which could then be shared outside your governance. It is critical to understand where your are exporting, the mode of transport (encryption in transit?) and where this information is ending up when it lands (encryption at rest).
Email: Typically everyone in a company has access to email and an email address. Attachments leaving your company or sensitive information in the body of an email are ripe for untracked data exposure. Phishing, further multiply the risk of financial or customer data falling into the wrong hands.
Download My Data: At the risk of being redundant much of the previous applies. However, be aware of this pervasive capability on mobile. The ease in which data can be downloaded is in everyone's hands.
Print: I am reminded of the movie Wargames where Matthew Broderick accidentally prints out the secret nuclear launch codes. While "far-fetched" the point is valid. Information can be printed out and with today's AI that information can be read in, parsed via phone, and be in a consumable file.
Confidentiality, data privacy and regulatory compliance are non-negotiable. As you integrate applications and AI into your firm, it’s essential to uphold the highest standards of security and governance. Here are the most important considerations:
Robust data privacy measures: Implement security protocols including encryption, data categorization, access controls, and audit trails to protect sensitive financial and client information.
Regulatory alignment: Choose your applications (Especially AI based) that embed compliance into their core design. It is very hard to implement after the fact. Tools today incorporate data protection regulations and accounting-specific safeguards from the outset, reducing risk and providing peace of mind.
Regular audits: Conduct ongoing audits to ensure continuous compliance and data security. This proactive approach helps identify potential issues before they become problems. This can be simple, don't overthink this task.
Tech Stack
Connect
Email: info@sonareon.com
© 2025 Sonareon. All rights reserved.
Phone: (248-602-2682
Schedule a time to meet with an advisor: Sonareon Schedule
Phone: 248-429-9110